The most popular topic currently is AI.
Most writers, assisted by some form of AI, will deal with the 1st round effects of AI. These consist in the immediate consequence of the use of AI in office work, medical and military applications, music and all producing or creative industries. As an economist you take the input – output matrix of the economy (OECD countries) and take AI as an additional dimension of this I/O matrix, for example. The result is an AI-augmented model of the economy. This 3-dimensional cubic view of the economy asks to reflect on the potential short-term and medium-term impact of AI.
Let’s take the example of translation and editing services. AI will in the short-term or the 1st round effects make it easier to offer mechanical translations with fast turnaround. Most likely, this will lead to less translators needed for routine translations of longer texts, which would otherwise be a very costly endeavour. The 2nd round effects, however, will make the expert knowledge of translators of texts, where every word counts, more necessary in order to provide the best version of a translation targeted on specific audiences.
In the legal domain, for example, the precision of words is primordial and errors can be very costly. Hence, the 2nd round effects of AI in this field will increase the demand for high quality translation services more than before the use of AI. The important shift consists in these 2nd round effects of AI, which give a push to multilingual societies as just one medium-term outcome.
Please use AI to read (listen) to this paragraph in your native language or even dialect using your favourite AI-tool. 
Augmented Cognition
With everybody talking about artificial intelligence we tend to overlook recent advances in augmented cognition. Just 2 examples of studies presenting new findings published in 2025 suffice to make that point. Automated versus manual driving have different effects on our brains. Automation makes us sleepy and inattentive with potentially dangerous consequences. Using EEG measures of neuromarkers the drop in attention shows up earlier than through measures of keeping one’s lane while driving. For jobs or duties that involve extended hours of attention the wearing of a mobile EEG-device could avoid lots of accidents. Drugs, alcohol or medication abuse would also show up before it is too late, I suppose (Scanion et al. 2025).
The 2nd study involved a robotic assistance to piano playing which achieved surprising training effects for learners of the music instrument. Objective measurement of speed and finger coordination might even allow overall accuracy to improve significantly. The technology around us and the one in direct contact with us, our behavior and performances shall have an impact on all of us sooner or later. We have to pose the question of how far we want to go along with these evolutions. Augmented cognition will not only be of interest for civil purposes, but military applications or dual use is evidently another option.

Top 5 Things T5T
Dealing with Elon Musk is a must these days (WSJ 2025-2-26 A4).
So it happened that on his way to Mars, Musk met God the almighty on his way back to heaven. Musk asked, whether he could join the ride.
God, not amused, asked Musk about his T5T (top 5 things) he accomplished in his life. Musk questioned God‘s right to ask this question and said he would tell the other T about this. God gave him just another day to come up with a response.
So here we are: the T5T Elon Musk might put forward:
(1) I created a million fancy electric cars.
God: Well, but there were already too many tin boxes on 4 wheels on earth.
(2) I created rockets that propelled billionaires into space and back again.
God: Your carbon footprint has exceeded a million people of the poorest countries on earth.
(3) I created a network of satellites that facilitated communication.
God: Nobody spoke to me yet using it.
(4) I bought Twitter and transformed the platform to spread evangelism of various sorts.
God: This has become a hoax spreading more lies than truth.
(5) I reformed the public sector employees to share my beliefs or leave.
God: This will ruin a lot of services like USAID, which have assisted me for many years in my caring and charitable service.
With all these T5T of yours in mind I am not sure I should let you return to that planet earth. Maybe I‘ll find another assignment for you where you can cause less harm Elon. Maybe, try “Waiting for Godot“.
(Image: instead of T5T try T4T (tea for two)) 
Quantification
The most obvious association with quantification is the attempt to quantify in the sense of measurement of situations, locations or social phenomena. This has taken considerable steps with the availability of smartphones that measure and thereby quantify all sorts of wanted and unwanted information about us. The distances walked are among the easiest to quantify. There have been many accounts and discussions about this kind of quantification. The results have been a further push towards self-optimization assisted by a quantification of almost all aspects of life. That is daily business of social sciences.
Quantification has another well-defined meaning to it, which is in physics. The revolution of the early 20th century has been to deviate from classical physics which assumed continuous processes in time and continuous measurements to the new world of quantum physics, another kind of quantification. This allusion is due to the Alain Aspect’s inspiring book “Si Einstein avait su” (2025) and his efforts to make quantum physics understood to a broader public. For me one of the merits of the book is the reminder that experimental physics can contribute and resolve many epistemological questions.
(Image: my popularized approximation of Schrödinger’s cat in Berlin Zoo)

Hallucinations
In the 21st century hallucinations have become a daily experience. The origins of the word can be followed back at least to the Latin verb “alucinor”, best translated with “to hallucinate”. As a verb to can conjugate it, meaning that I can do it, you can do it, s/he can do it, and we may do it in groups. Roman emperors did it, American presidents do it and, of course, AI does it. Hence, it is a great subject to study.
In “Nature” 2025 we find ways to limit hallucinations of AI systems. The strategy consists mainly in repeated queries of the same type, but from different angles. It is a bit like cubism applied to informatics. On “github.com” we can follow the rankings of AI-models using LLMs based on the “hallucination-leaderboard” developed by Vectara. On “huggingface.com” you can test the Hughes Hallucination Evaluation Model. For example it is possible to run a test of your own small text documents (just like any blog entry on this webpage) and what the AI systems will do them in an attempt to summarize your ideas. According to the “hallucination-leaderboard” we are confronted with a 1.3%-4% hallucination rate of the top 25 LLMs as AI-systems. In text based systems the quantity of “errors” is a first indicator only. The seriousness of the omission, addition of wrong information or an erroneous judgment will be left to the reader or analyst to uncover.
There is now a lot to do to test various AI-systems on their “trustworthiness” in summarizing my own work. My very own daily hallucinations have become a large data base as a test case for the capacity of LLMs to make sense of them.
Based on the series of passed blog entries I shall test the capacity of AI to predict the n+1 blog entry. It would be great to know today what I am going to write about tomorrow etc. Thanks to AI I shall have (finally) a sort of intellectual life after death (not sure whether I should want this). Enough of hallucinations and on hallucinations for now, back to serious readings or fictionalized science. (Image: extract from Delphine Diallo, Kush, 2024 at Hangar Gallery Brussels). 
Space Missions
As we realize that critical infrastructure on earth is not safe in times of military conflict, space missions have become an additional form of competition between countries, continents and alliances. India has accomplished in January 2025 the coupling of 2 space satellites. The level of technological knowledge to achieve the coupling and decoupling of satellites included among other competences the mastering of algorithms that control sensors and propulsion. Beyond the communication cables on earth, satellites can assure telecommunication services, if other networks are interrupted.
The Indian Space Research Organisation (ISPO) has announced the successful “space docking experiment” (SpaDeX) and joins the other 3 countries US., Russia and China as the 4th country to achieve this. The race in space and to space beyond earthly competition shifts attention also to the additional category of a race to technological innovation and applications of those. Since the war of Russia in Ukraine we know about the “dual use” factor (civil and military) of satellite technology. Satellite images of your own country are helpful in many respects ranging from weather forecasts, rain, draughts and habitat changes or population movements. Early warnings of flooding are surely important civil applications. Movements of military equipment by potential enemies are much needed early information, which increases warning time spans. With more satellites in space the good as well as the dangerous potential is expanding. Sovereignty in the 21st century certainly has a technological dimension. Therefore, the demonstration of satellite coupling in space accomplishes not only a dual use achievement, but also fulfils a triple use or ambition. The 3rd one is political. Hey, look we are also watching you, or might do so.
(Image: Robert Indiana “Imperial Love” 1966/2006 in Berlin Neue Nationalgalerie) 
Game Tech
Gaming has moved digital and online for a long time. Networked gaming and following the best gamers online on video-platforms like twitch has captured a lot of attention from younger generations. With a real trend of gamification for industry and even public services, the digital gaming sector is moving from backstage to front end of companies and services. Public administration as a game. Enjoy the use of a public service through a game-like experience. Walk around in the metaverse world and get your admin work done. I would love to have such an experience. There are so many applications for gamification that the bottleneck is in the human resources to program all these applications. Coding the digital and virtual worlds to get real stuff done is just around the corner. The SCCON 2024 in Berlin showed these technologies next to each other. 2025 we might see integrated prototypes. I have a digital dream, others call it a vision for public services in the 21st century. 
Move Tech
First we teach robots how to move. Next, they teach us how to move and motivate us to do more. This is not only for the elderly persons to imitate the moves and talk to AI systems, but children too will have fun and learn new tricks from robots rather than old dogs. Learning languages with an AI system is well advanced. Soon we shall walk with our artificial friend around cities and have a perfect tourist guide with us. Imagine walking in the countryside with your robot explaining you the flowers and herbs next to you. These brave new worlds are not too far off and it is up to us to be open to accept or dismiss these applications. Coaches using ball throwing machines or robots have managed to lead pupils to higher levels of practice faster than others. Motivation through move technology has undeniable advantages. 
Ed Tech
Education Technology is much more than the use of tablets and Internet access in schools or in each classroom. Some schools revert to ban mobile phones access during classes or introduce specialized social media breaks during the school day. At the other end of the intelligent use of digital technology is the digital classroom with digital whiteboards in each classroom or the first fun hands-on experience with coding for primary school pupils through, for example, the “Scratch” platform. Once you are used to the power of the whiteboard to use web-based information in teaching systematically, most teachers and pupils will no longer want to miss these tools. Public libraries become important access points for those who have no speedy access at home to assist in learning. Digital tools and e-learning are an empowerment of learners to benefit from the millions of useful learning tools and platforms on the web. A first understanding of easy coding allows children to figure themselves as producer of games rather than only a consumer of fantasy games. Create your own story instead of following the stories of others is empowerment. Scratch it, if you like. The role of the teacher in classrooms is evolving fast as well beyond the 40-60 minutes slots in class. Play the games of your pupils, is a bit like a flipped classroom.
(Image: SCCON Berlin 2024 connected classroom simulation) 
AI Nobel
Artificial Intelligence has made it into the ranks of Nobel prizes in 2024. As AI is been talked about everywhere by now the Nobel Committee has deemed it expedient to award Hopfield and Hinton the Nobel Prize not in informatics, this does not exist (yet), but in physics. Neural networks focus on the links between bits of information rather than just the sheer number of data points mimics the functioning of our brains. The most remarkable statement by Hinton is probably the one of the also dangerous potential of this invention. He has already issued a disclaimer on the potential of AI in warfare or other ways to impinge on our human idea of freedoms. The discovery of the applications, good and bad, of these AI-based systems has just begun. The comparison with Nobel‘s original discovery and mass production of explosives from which the prize draws its name has hardly been more adequate recently. (Image stockholm City Library)

Smart Cars
Technology of cars and in cars has evolved rapidly with the move towards the smart cars. Smart cars are characterized by many additional sensors, almost permanent connectivity to the producer’s software platform, the internet, autonomous driving capability or, potentially, remote control. We might still curse some nostalgic feelings of being in driving seat, but the supervision of our capability to drive and monitoring of behavior has reached impressive levels of perfection beyond the fasten your seatbelt sign and alarm. The software that is driving our cars has become the challenge of the coming years and with this the concern for data privacy and cyber security. Smart cars have multiple cameras to guide driving and parking effectively. These cameras are also a perfect spy even around or in your home. From our smartphones we all know the scanning of connectable Bluetooth devices or wlan nearby. Smart cars are powerful assistants in data collection sometimes even beyond your control, for example who these data are sent to. June Yoon (2024-10-2 Financial Times) has developed this rationale even further to stir up additional fears: “A hacked self-driving car might even be turned into a weapon”. The weaponization of beepers, talky-walkies is certainly not the last step in this process of potential dangers of technology. Smart cars come with additional risks, not only additional comfort. Better choose your rollercoaster wisely. 
Knowledge Work
In the social sciences the term knowledge work defines the group of professions that deal with and deal in knowledge. Most of them are in academia, but there are many other professions like ICT professionals or lawyers that used to shuffle paper who now work all digital. Hence the relatively new addition to the sociological vocabulary is “mobile knowledge work”. We, and yes I am part of this group, can do our job from almost any place with a stable internet connection. Breda Gray et al. (2020, Made to work: Mobilising contemporary worklives.) highlight the importance of gender considerations when we study these new forms of work. Similarly, social class and cultures of more or less trust are thriving for independence. This will play a role in who choses these new forms of work. The digital technology enterprises, media and social media workers are and will be the forerunners of this change. The education sector and academics in general have followed suit.
The issue of autonomy has also received some attention by the authors and this is likely to be a big challenge to standard work relationships as we knew them before the digital turn and the Covid-19 pandemic. The mobile knowledge workers were the first to insist on change of work practices, there will be other professions that will strive for greater autonomy of various kinds.

LED light
For decades now, we have the LED light technology around us. In many instances we do no longer realize the presence of light emission devices (LEDs) for example in our television screens or in road lighting. However, this still is an exciting field of electrical engineering and the replacement of gas lighting as well as other electrical devices with higher energy consumption are high on the agenda for sustainable lighting. There are important health and security aspects related to lighting (sleep and road traffic).
In Berlin the demonstration and test area for innovative LED lighting is also an open-air museum which can be experienced throughout the year. The party-goers and club visitors might best know the demonstration street as part of the “Deutsches Technik Museum” The energy saving potential of LEDs use in street lighting is substantial and should interest most rural and city councils. The demonstration of the differential effects of targeted lighting and broad illumination based on the same technology is impressive. Of course, the design aspect of LED-technology with the colourful potentials are of interest beyond the technical aspects to replace for example gas lighting. There is much more to lighting than just opening your eyes in the morning. (Image FG Lichttechnik TU Berlin) 
AI Ghost Writer
Yes, with AI we have entered a new phase of the impact of IT. Beyond the general applications like ChatGPT there is a rapidly expanding market of AI applications with more specialized functions or capabilities. In the realm of scientific writing AI-Writer is an interesting example of the AI assisted production of scientific tests. After the specification of the topic you will receive several options to specify the content of the short paper you want to produce with AI-Writer. You may choose the headline, keywords, subtopics and the logical order of these subtopics depending on your audience. Alternatively, you leave all those decisions to the application and restrain yourself to fix the amount of words you would like the paper to have.
AI-Writer is a powerful ghost writer for much work even of advanced scientists. The quality of the paper needs to be checked by yourself, but the explicit list of references, from which AI-Writer derives its restatements of the content, is just next to it. Your ghost writer AI is likely to replace a number of persons that were previously involved to just produce literature reviews or large parts of textbooks sold to millions of students.
A much lesser known feature of such tools is the way it makes plagiarism much more transparent for the scientific communities and the public at large. These programs demonstrate the techniques of combining knowledge and the citation imperatives in a transparent, almost pedagogical way. This latter function will speed up scientific work like dissertation drafting, since the reading up and documentation of previous literature in a field is a time consuming early stage of academic degrees.
Email composition, rewording, plot generator or social media posts are additional nice-to-have features of the new AI-assistants. A lot of work that has been outsourced, for example, to lawyers, consultants or other technical professions, might equally be challenged. Ghost writers have been around for centuries. With AI for everybody, they will also be involved everywhere.
(Image screen shot of working with AI-Writer 2024-6) 
AI Reader
In the middle of the hype around AI it is useful to take stock of the reflection and evolution of AI. In my own analyses and writings on AI it evident that a narrowing of focus has taken place. Whereas before 2022 the writing dealt more with digital technologies in general. The links to the literature on the social construction of technologies was obvious. Algorithms and AI was a part of the broader topic of society and technology.
This has changed. The public debate is focused on “everything AI now”. We look at technological developments largely through the lens of AI now. Hence, my focus of assessments of technology from a societal perspective follows this trend. In a collection of blog entries on AI we try to demonstrate the far reaching changes that have started to have an impact on us. In the last few months the all encompassing concern about AI’s effect on us needs full attention of social scientists, policy makers, companies and the public at large. We can no longer leave this topic to the software engineers alone. By the way, they themselves ask us to get involved and take the latest advances in AI more seriously.
As a “flipbook” the online reading is rather comfortable (Link to flipbook publisher MPL). The pdf or epub files of the blog entries allow to directly follow the links to sources in webpages or other publications (AI and Society 2p 2024-4-18). The cycles of analyses and comments have become faster. Traditional book writing suffers from time lags that risk to make pubications outdated rather quickly. Dynamic ebook writing might bridge the gap between time to reflect and speed to publish or inform the wider public. The first update as .pdf-file is available here: AI and Society(2).


Digital organising
Since the digital innovations continue to broaden our scope of how to organise, we have to make conscious choices which way to choose. The traditional form of sending out newsletters and waiting for responses is still a feature that is prevalent across Europe. Most organisations have shifted to digital plus physical versions by now, just like newspapers. Young organisations by founding year have started or shifted to digital only for speed of delivery, CO2 and cost saving mainly. We may derive a first dimension of organising between the digital and physical. 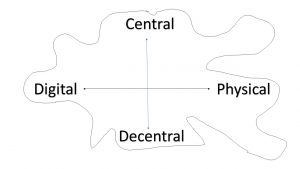
A second dimension consists in the central versus decentral forms of organising. Similar to the franchise principle of organising companies, organisations have a choice to keep a central structure with varying degrees of freedom at the regional, sectoral or local level. Organisation theory is helpful in this respect. Various hybrid forms are equally possible. Centralised in financial aspects, but scope for local decisions on content.
Bohn et al. (2023) define digital organising as “collective purposeful alignment and distributed action fostered through digital technologies”. Centralisation and/or Decentralization become a matter of conscious choice. The processes of datafication and connectification, whereby every bit of information becomes a data point and any electronically enabled device can be connected with each other. Organisations now have a choice of how to organize including digital organising. The opportunities are within the space opened up by the 2 dimensions (figure below). A specific subject matter may require more physical presence and maybe centralised structure, but digital only forms with highly decentralised forms are powerful tools in the 21st century. New as well as established social movements may well take advantage of these digital technologies as well. (Image: Digital Organising 2024 Protest Berlin). 
AI and Behavior
We start to analyze the impact of AI on our behavior. It is an important question to be aware of not only how we interact with AI (Link), but also what effect the use of AI (disclosed or not) will have on our social behavior. Knowing that AI is used might change our willingness to cooperate or increase or decrease pro-social behavior. The use of AI in form of an algorithm to select job candidates might introduce a specific bias, but it can equally be constructed to favour certain criteria in the selection of candidates. The choice of criteria becomes more important in this process and the process of choosing those criteria.
Next comes the question whether the announcement includes as information that AI will be used in the selection process. This can be interpreted by some that a “more objective” procedure might be applied, whereas other persons interpret this signal as bad sign of an anonymous process and lack of compassion prevalent in the organization focused mostly on efficiency of procedures. Fabian Dvorak, Regina Stumpf et al. (2024) demonstrate with experimental evidence from various forms of games (prisoner’s dilemma, binary trust game, ultimatum game) that a a whole range of outcomes is negatively affected (trust, cooperation, coordination and fairness). This has serious consequences for society. The social fabric might worsen if AI is widely applied. Even or particularly the undisclosed use of AI already shows up as a lack of trust in the majority of persons in these experiments.
In sum, we are likely to change our behavior if we suspect AI is involved the selection process or content creation. This should be a serious warning to all sorts of content producing media, science, public and private organizations. It feels a bit like with microplastic or PFAS. At the beginning we did not take it seriously and then before long AI is likely to be everywhere without us knowing or aware of the use. (Image taken on Frankfurt book fair 2017-10!)
Sleeping
Sleep is a process. That is why it is best to talk of sleeping rather than sleep. There exists abundant research on sleep and more and more acknowledge the process-like characteristics of sleep. The medical literature deals a lot with sleep apnoea, which constitutes a serious health condition. Time use surveys establish links between daily activities and sleeping for example. The social context is another influence on sleeping. Friends and family co-determine sleeping patterns as well. The latest better understood impact on sleeping depends on the use of technological devices before and during sleeping. Smart phones reveal themselves as not so smart if it comes to the quality of your sleep. At least this the result of the study on „bedtime technology use on sleep quality and excessive daytime sleepiness“. It yet another field in which technology is slowly creeping under our skin and we have to learn how to handle negative side effects before they endanger our physical as well as mental health. Bedtime routines or reading without a screen before falling asleep appears to be a worthwhile way to improve sleeping. Worth trying out again and again.

Styles are a Changing
We all have our very own style. Even if you believe you have no style, then this will be your style. Of course, styles are changing continuously and fast fashion tries to make us believe we even ought to change as frequently as possible. Just find your style no matter of age and gender. Yes we can. Young designers test new materials and cuts to make new impressions. As science is progressing with new fibers that imitate the apparently light fur of polar bears, new designs will become feasible and enrich the list of potential fibers in clothing. In addition to seamless 3D knitting the new fiber allows to replace down with light fiber. Going out into the cold will be fun again. Want more of this, visit Fashion in Action! (Image from empty space designers webpage 2023-12-24 Berk and Julien).

Trending
Some cartoonists or scientists have a special capacity to sense and to explain upcoming trends. Put in a humoristic form the audience you are likely to reach will by far exceed the numbers you might reach otherwise. Loriot had a gift in this respect which is much acclaimed in Germany. Taking issue with the obsession of driving a car and all sorts of topics related he foresaw the trend to massive expansion of road traffic and what this trend, if extrapolated, will do to us. Mankind will change, men will no longer be kind. We return to animal-like behaviour and become slaves of the new technologies we create. Bad weather at least makes us rethink our mobility patterns. 
Emergencification
Particularly around holiday seasons across the whole year we observe the “emergencification” in modern societies. This not so new trend consists in the strategy to artificially create emergency situations in which it is considered reasonable to ask for higher prices. It appears to be just another kind of a “greedflation”, whereby extra profits can be reaped due to shortages of food or particular forms of energy. Medical services have also pushed for an emergencification of their services due to ever longer waiting queues for appointments and treatments. The strategy here is easily disclosed. (1) You decline any appointment earlier for inspection of cars, heating systems, office equipment or medical check-ups and sooner or later a “planned” emergency will arise, which allows you to charge higher prices than the routine in time appointment or treatment. This makes prevention of more costly interventions far more difficult. In sum, the costs to society as a whole rise by the simple way of emergencification.
Even using a repair platform, we did not receive a single offer for a more lengthy and costly repair of my 10+ year old car. Hence, we just wait for a breakdown with more serious and costly consequences. Unfortunately, the same holds true for many medical services. If you no longer manage to assure a timely consultation you are more likely to go directly to the emergency services of a hospital. This is then the costly, but only alternative left to you. In the artificially created emergency you have little room for negotiation and a choice of different offers and conditions. It is a shift in negotiation powers to the service provider. The emergencification creates a price inflation of a specific kind. Worryingly, this kind of inflation is well beyond the normal statistical measurement of inflation national statistical offices observe. In addition to the much debated “greedflation” we should deal with the emergencification as an additional price mechanism. Just ask about examples among your friends or in the neighourhood whether they have lived through an example of emergencification. The stories are abundant and full of surprises. The example I heard: “birth and death, both come as a surprise or emergency, and yet we have the whole life to prepare the latter one”. Part of image taken from “Loriot “on the pleasures of driving (2022. Subtitle:” I suppose the screen wipers caused the trouble”.
Nachhaltigkeitskonzept
Ein Nachhaltigkeitskonzept gehört zum Bauen mittlerweile wie das Gelbe zum Ei. Die Einreichungen zum Realisierungswettbewerb eines Portals für das Deutsche Technik Museum Berlin hatten entsprechende Anforderungen zu erfüllen. Für ein Technik Museum können dazu die Anforderungen schon etwas höher sein und die oft geforderte „Technologieoffenheit“ oder die Diskussion darüber zumindest andeuten. Der Anerkennungspreis ging an ein Konsortium für die Einreichung 1110, die eine klare Übersicht ihres Nachhaltigkeitskonzepts vorstellten (siehe Auszug Image unten, Foto aus der Ausstellung 2023-12). Nachwachsende Baustoffe gehören zum Repertoire. Gleichzeitig sollte die Erhaltung oder gar Förderung der Biodiversität Teil der nachhaltigen Konzeption sein. Innerstädtisch ist die Rückumwandlung der Versiegelung der Böden eine wichtige gesundheitsfördernde Bauweise. Kühlung in den aufgeheizten Städten ist durch Grünflächen und Beschattung zu erreichen. Tolle Architekten sind das, die den Mut aufbringen den Stachel in die Wunde zu legen. Die Anwohnenden und Besuchenden würden es den Verantwortlichen jahrzehntelang danken.
Das sind längst keine abgefahrenen grünen Ideen oder Träumereien mehr. Paris hat es schon längst vor gemacht. Ganz nah beim Eiffelturm ist das „Musée du Quai Branly – Jacques Chirac“ das als Neubau mit Garten vom konservativen Präsidenten Jacques Chirac eine grüne Naturoase mitten im Herzen Paris hat bauen lassen. Es ist immer noch eine Art Geheimtipp für Pariser in den zu warmen Sommermonaten. Berlin könnte wie mit der vom Pyramiden-Architekten Pei geplanten Eingangshalle vom Deutschen Historischen Museum mal wieder mit einem Nachhaltigkeitskonzept mit Paris gleichziehen. Gemeinsam können wir auch nachhaltig. Mit der vom Menschen und seiner Technik verursachten Erderwärmung haben die nachfolgenden Generationen noch lange genug zu kämpfen. Mehr Nachhaltigkeitskonzepte braucht die Technik. Das ist die wirkliche Herausforderung des 21. Jahrhunderts. 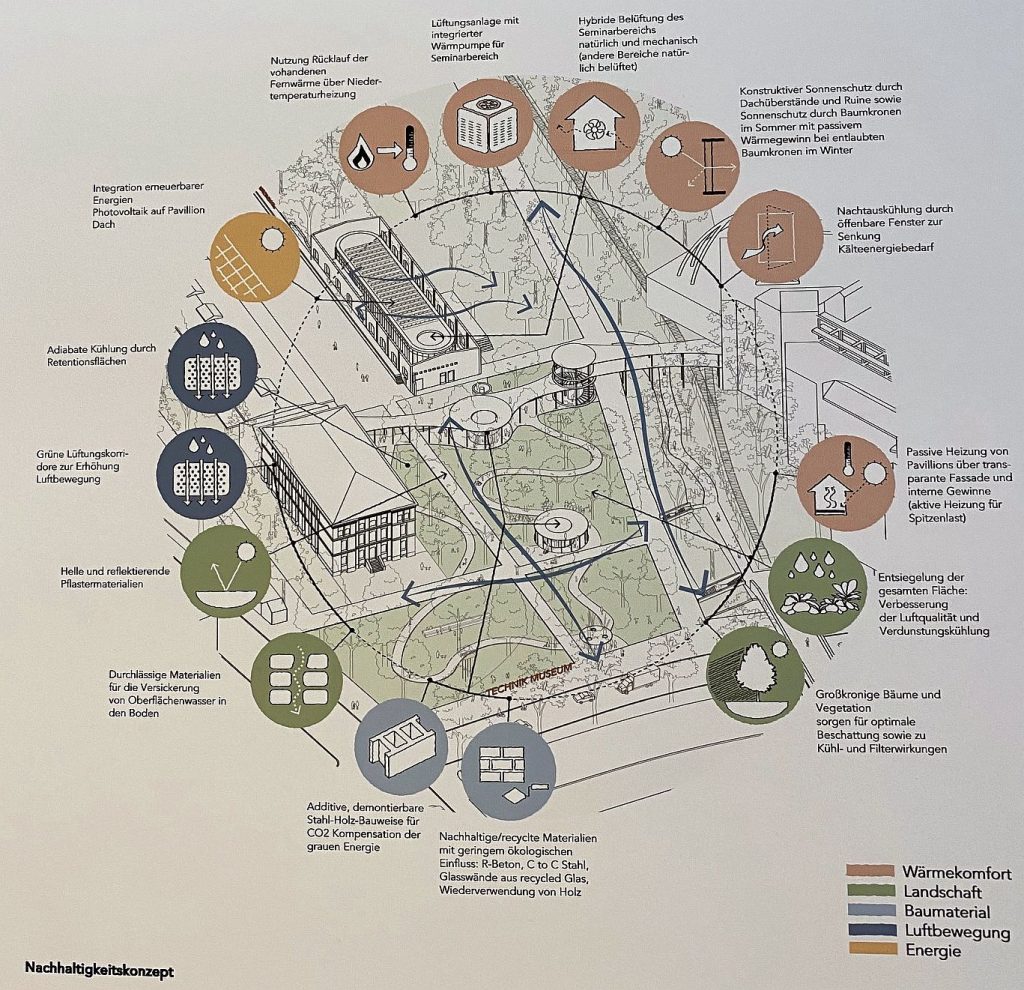
Technik Museum
Wir müssen die preisgekrönten Bauprojekte von Berlin nicht alle mögen. Die „schwangere Auster“ (Haus der Kulturen der Welt) war anfangs auch nicht beliebt, aber trotz Einsturz, haben wir sie lieben gelernt. Neben die Neue Nationalgalerie geplant von Mies van der Rohe und der Berliner Philharmonie von Hans Scharoun reiht sich bald die sogenannte „Scheune“. Ja ,eine multifunktionelle Verbindung der Museen ist im Bau. Nicht viel weiter werden wir vielleicht schon bald wieder eine kleine Erinnerung an die Berliner Mauer bestaunen können. Unweit vom Kulturforum stehen einige unverbundene Solitäre, die zusammen das Deutsche Technik Museum formen. Das ist bisher nur wenigen Touristen im Vorbeifahren auf der Ost-West-Achse in Berlin aufgefallen. Daher braucht es jetzt eine „instagram-able“, gemeinsame und verbindende Häuserfront, vielleicht so etwas wie die Pyramide (Pei-Bau) mitten im Louvre.
Die Einreichungen zum ausgeschriebene Realisierungswettbewerb (Link zu pdf-file) mit ziemlich konkreten (technischen) Vorgaben können noch in 2023-12 in einer kleinen Ausstellung eingesehen werden. Das gab es auch vorher schon anlässlich des Wettbewerbs für die Scheune. Wir hatten also keine großen Erwartungen, aber es hätte doch dieses Mal anders kommen können.
Der Blick auf die Pläne, Modelle und beschreibenden Texte hätte durchaus mit etwas Mut der Jury anders ausfallen können. So werden wir wohl mit dem 1. Preis des Realisierungsvorschlags leben lernen müssen. Mit etwas Abstand als virtueller Besucher im Modell kam mir direkt die Assoziation ich stehe vor einer Mauer. Diese ist aber im 21. Jahrhundert aus Holz und mit Solarzellen bestückt. Die „Deutschen Baumeister & Architekten“ erlauben auf ihrem Blog eine Vogelperspektive auf den prämierten Vorschlag. Die Pressemeldung der www.bim-berlin.de erläutert umfänglicher die Ausschreibung und die Begründung der Jury (Link).
Neben den 3 Preisen wurde noch 2 Anerkennungen mit Preisgeld ausgesprochen. 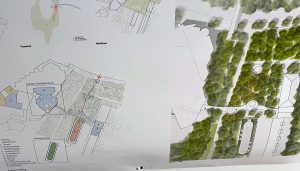 Die Nr. 1110 imaginierte eine naturbetonte Umsetzung, die die Technik visuell in den Hintergrund verschiebt. Sie setzt einen wichtigen Kontrapunkt zur Technikverliebtheit in den Nachbargebäuden. Worum geht es bei der Technik? Richtig, letztlich um den Menschen und seine Lebenswelten. „Bionik“ beispielsweise ist Technik, die die Natur zu Rate gezogen hat. Das ist in der Forschung und Entwicklung von Technik ein riesengroßes Thema. Aber wir können dafür doch wieder ein eigenes Museum bauen. Bisweilen können wir und alte Computer und Telefone im Technik Museum ansehen. Klar Autos gibt es auch. Die Spannung Natur und Technik wird uns sicherlich noch einige Generationen lang beschäftigen.
Die Nr. 1110 imaginierte eine naturbetonte Umsetzung, die die Technik visuell in den Hintergrund verschiebt. Sie setzt einen wichtigen Kontrapunkt zur Technikverliebtheit in den Nachbargebäuden. Worum geht es bei der Technik? Richtig, letztlich um den Menschen und seine Lebenswelten. „Bionik“ beispielsweise ist Technik, die die Natur zu Rate gezogen hat. Das ist in der Forschung und Entwicklung von Technik ein riesengroßes Thema. Aber wir können dafür doch wieder ein eigenes Museum bauen. Bisweilen können wir und alte Computer und Telefone im Technik Museum ansehen. Klar Autos gibt es auch. Die Spannung Natur und Technik wird uns sicherlich noch einige Generationen lang beschäftigen.
(Image: Auszug aus Unterlage und Würdigung des Anerkennungspreises BIM, 2023) 
Twitter Retreat
There are many migrating species in nature. Birds form a large part of the them. This follows a kind of annual or seasonal pattern. Depending on the migration experience and dangers some, sometimes many don’t come back. This seems to describe the migration experience of the tweeting bird called twitter. Changing the name from Twitter to X, whereby X for maths-oriented people stands for a variable name that can be filled with any value. For the cinema industry X stands for x-rated adult only content and has rather obnoxious content. This might hold for web content as well.
Online through “https://netzpolitik.org/2023/x-odus-immer-mehr-medien-machen-schluss-mit-twitter/ the disastrous consequences of harsh human resource policies and lack of political sensitivity can be followed. Multiplying biased opinions of right-wing extremists, the platform has been highjacked and many tweeting birds leave or have left already.
Leaving is not easy though. People and enterprises have invested substantial amounts of money into tweeting and software developers have created specialised features to make it easy to spread press releases or info via these add-on services. I myself benefitted from services to show my tweets on my webpage or to easily publish info or links to the webpage. As of now, with migrating away most of these investments will be lost. It was smooth and easy, but now we start this all over again with other comparable platforms and assistance from developers. Mastodon and Bluesky are on the rise as alternative platforms and most likely we shall use both for some time just like Netzpolitik and many others. If already 1/3 of users intend to leave Twitter/X the impact of big advertisers leaving the platform has even more impact. After all they pay for reaching potentially millions of platform users, but now they reach only a steeply biased subset of previous users. Deleting the Twitter/X app saves you from other potential unwanted monitoring or tracking. Only the addresses on Mastodon for example are a bit longer like @mastodon.social@klausschoemann. Decentral monitoring of illicit undesirable content has advantages and disadvantages. We shall have to monitor this a bit ourselves and contribute more actively to save such platforms from bad weather or seasonal migration. 
Over a generation the association with the word mail or AI has changed. Younger generations will automatically think of email as the obvious association with “you have got mail”. Asking people for their mail address, most people will respond immediately with their email account. That has certainly changed over the last 20 years. Email has become extraordinarily important for contacts, content and “crime”. The original set-up of mail servers were supposed to exchange data and information between trusted and trusting individuals. Nowadays we have become “anyone” on an email-list or part of a cascading email-chain. Pishing emails that try to lure us to potentially fake webpages to enter personal information is widespread. A whole new industry of cybersecurity has evolved in parallel with ever faster pingpong of new threats and costly remedies. Most critical remains the human factor to protect email and vital information from abuse. All training to better manage email should therefore begin with awareness building on the need to take cybersecurity seriously right from the beginning. It is not an issue to deal with towards the end of learning about it. Some general points have become common practice. Think carefully if you need to open the mail. Check whether there are external links in it. Do you really need this extra information? Be careful about the number of persons you forward or put in the copy field of your mail.
Unfortunately the simple mail transfer protocol (SMTP) makes it technically fairly easy to abuse email addresses and send an email from a domain name which you do not own. Same holds true for the content of emails. Originally only basic letters and numbers were allowed, no Umlaut etc. But then the “multipurpose internet mail extensions” (MIME) enabled more formats of attachments and illicit links and files within the email content.
In consequence it became necessary to scan emails en masse for malware and obnoxious content. Hence the quality of your email programs reveals itself with the amount of spam you still receive. Next come the email filters that sort your inbox for spam and other modern plagues like unwanted newsletters or notifications.
In consequence we sometimes wonder that we never received certain emails albeit the person sending it reiterated that the email was sent. Even checking your spam folder in the email program might not solve the issue because your receiving email server has been instructed not to accept emails from previously unknown mail servers. Not much you can do about this as an individual person, you mail server is just not on the so-called white list from which to accept incoming emails.
With a mail address from the big national or international companies you have little to worry about in this respect. Smaller companies or organizations might suddenly face a thorny issue if their i@xy.z address appears on a dubious list. You will end up sending but nobody receives your emails. It might take you quite some time to find out about it and even more to fix the issue. Hence the take home message is, have more than one email address registered on different mail servers to check that sending out and receiving emails works properly for you. Managing an own webpage with email service for members or employees is a nice service, but beware of the implications for cyber security as well.

Cybersecurity
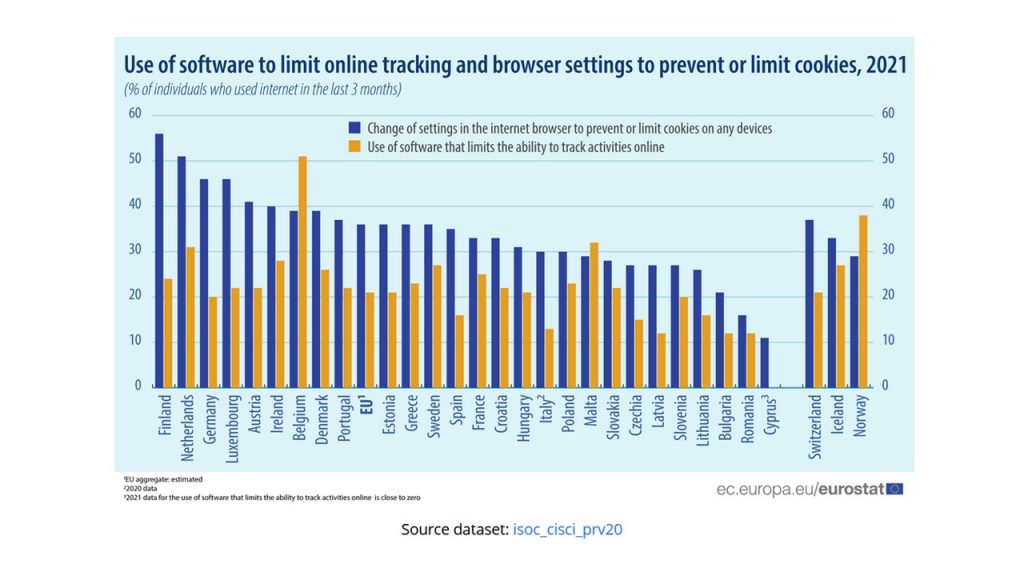
Der letzte europäische Monat der Cybersicherheit hat wohl kaum zu einer nennenswerten Verbesserung der Situation der Cybersicherheit geführt. Beispielsweise der Tankstellenzulieferer mit Öl, die Oiltanking aus HH, hat einen Cyberangriff nicht abwehren können. So wird die wahrscheinliche RansomWareAttacke wohl erst nach Zahlung in Cryptowährung wieder zu vollen Funktionalität zurückkehren können. Scheinbar können zwischenzeitlich die Preise nicht geändert werden und es sind keine Kartenzahlungen möglich. Zusätzlich waren belgische Häfen betroffen. Der internationale “safer internet day” zeigt ebenfalls wenig Wirkung. Wer wichtige Passwörter heute geändert? Eben.
Eurostat hat passgenau zumTag die Statistik zur Verwendung der Internetbrowser und deren Sicherheitseinstellungen veröffentlicht. (s.u.). Auch die sehr offene Volkswirtschaft Deutschland hat da noch einiges zu tun, besonders bei der Verwendung von spezifischer Software. Die wissenschaftliche online Zeitschrift “Frontiers in Psychology” hat eine kleine Studie mit 333 Studierenden veröffentlicht bei der das Konzept “Techno-Stress” angesprochen wird. Also die großen Konzerne der Internetgiganten (GAFAM) verursachen bei fehlendem Datenschutz (DSGVO) bei Nutzenden erheblichen “Techno-Stress”. Zoom-meetings und Ransomwareattacken etc. haben sicherlich das Stresslevel nochmals erhöht, gerade für diejenigen, die selten TechnoMusik hören.
Passwortmanager erlauben es, komplizierte Passwörter zu vergeben und zu verwenden. Machen müssen wir das selbst, die Geschäftsmodelle der Internetgiganten basieren auf unserer Trägheit und Unwissenheit. Damit lässt sich richtig viel Geld verdienen.